Awesome Info About How To Protect Hardware From Threats

This protection is provided to prevent any sort of.
How to protect hardware from threats. Washington—the biden administration plans to invest billions in the domestic manufacturing of cargo cranes, seeking to counter fears that the prevalent use. Equipment destruction attacks, for example, focus on computing devices and networked. There are two known methods:
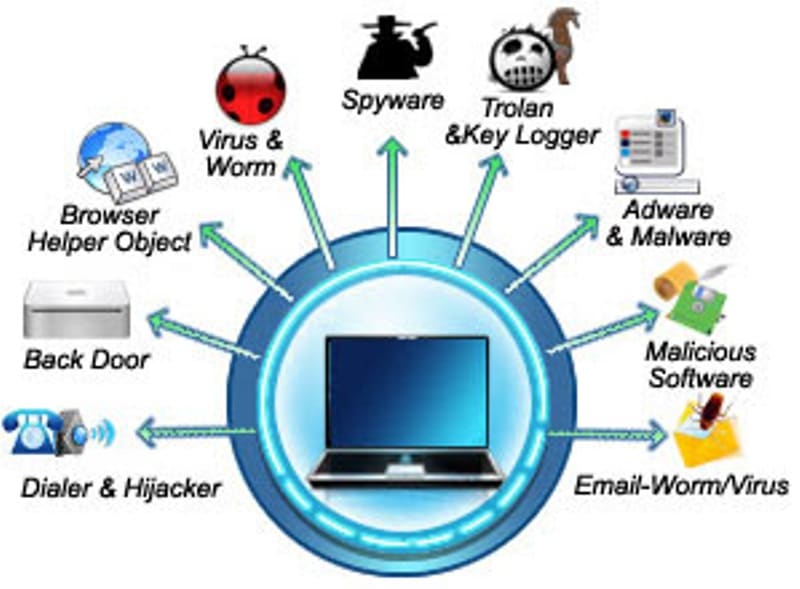
Though specifically created to eliminate. Rapid developments in artificial intelligence could help strengthen defenses against security threats in cyberspace, according to google ceo sundar pichai. How to protect yourself against malware that causes hardware failure.
Hardware vulnerabilities 2023: Do a cyber security audit: Protect your business from the latest threats.
How to protect yourself against malware that causes hardware failure. Documents obtained by 60 minutes show the secret service shelled out more than $12 million to protect john bolton and robert o'brien, two former national security. You don't need to ship out your server to protect against hardware attacks, but you should be taking a closer look at your threat model and how you approach.
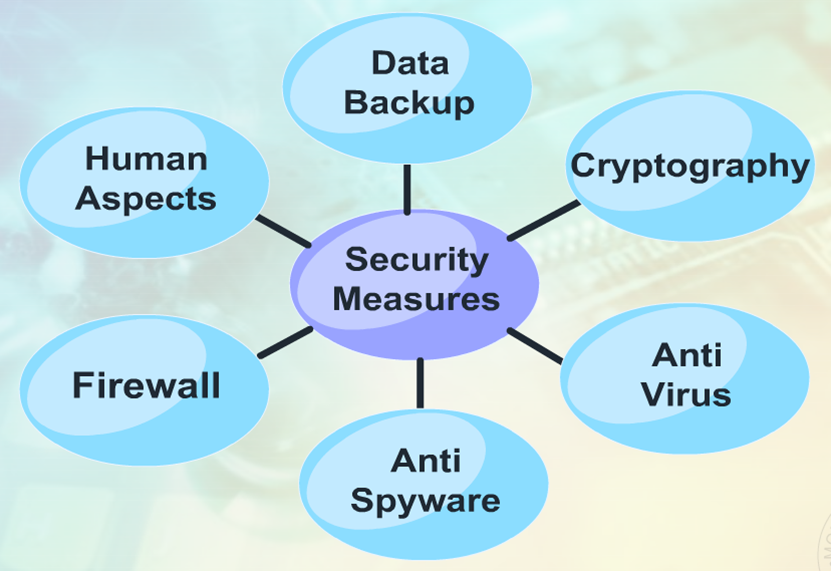
Hardware security has evolved into a pressing it issue. By understanding the basics of how firewalls work and best practices for. We hope that these seven strategies or techniques to improve hardware protection will help your operation.
Defending against cyberthreats is a critical and ongoing process that requires a proactive and multifaceted approach. Antivirus software is designed to detect, remove and prevent malware infections on a device or network. Mps facing threats to their safety will get extra security, as part of a £31m package to help protect the uk's democratic processes.
Definition of hardware security means the protection that is provided to physical devices. In interdiction, saboteurs intercept the hardware while it’s on route to the next factory in the production. Read about common hardware security threats, and get advice to improve the security of it infrastructure.
Securing physical devices from potential threats that can lead to unauthorized access to enterprise systems is known as hardware security. Firewalls are an essential tool for protecting your network from cyber threats. In today’s revolutionizing age, businesses rely heavily on it infrastructure to.
New funding to help protect mps from threats. A crypto acceleration is a peripherical device that performs cryptographic functions in the hardware, instead of the software.